
Mechanical keyboards have become more popular than ever. Yet many are prone to chatter —keystrokes registering more than once per keypress. That is, unwanted repeated letters as you type. The basic problem is that all mechanical...
Stuxnet and the Birth of Cyber War
Most people are aware of the horrors of nuclear war. However there is much less awareness of the civilisation-ending potential of cyber war. Stuxnet is one of the most famous and sophisticated pieces of malware...
Byte.Yoga – A New Name for this Blog
Exciting News: Codewiz.au is Now Byte.yoga! Dear Readers, We're thrilled to announce a significant update that marks a new chapter for our blog. As part of our ongoing evolution and commitment to bringing you the best...
To help with my Cybersecurity job search, I thought it would be interesting to see how much pentesting I can learn in a one-week period. I'll describe what I've done, starting from the basics. I'll...
Welcome to Byte.Yoga
New Website Byte.Yoga is a new website which will be featuring information, tips, advice, ideas, and a bunch of other topics mostly related to IT and Cyber Security. Why Another I.T. / Cybersecurity Website? Considering that...
This page describes setting up a CFML server using Lucee (compatible with Adobe ColdFusion CFML pages) on Amazon's AWS EC2 cloud computing service. I was looking for a way to host example/demo versions of some of...
This page shows the code for a "Load More" button, using jQuery and AJAX. It can be used to add any content to a <DIV> inside web page while the rest of the page is...
This page demonstrates a simple quiz written in JavaScript and HTML forms, made for a TAFE course in web and database development/design in 2001. This kind of quiz makes a good project to practice on when...
How to Install Kali Linux On VirtualBox
How to Compile C Programs for DOS in 2021
Learn How to Hack Systems By Playing the Bandit Wargame
Easy Clock With Seconds On Windows 11
This is the best method I could find to easily obtain for myself a precious and coveted semi-Windows-10-style clock on Windows 11. Microsoft seems not to want us to know the time in seconds. I'm not...
This page describes how to install bee-box, a virtual Linux installation containing bWAPP, which is a deliberately buggy web application to practice pentesting and other cyber security skills on. From the bWAPP website: ...

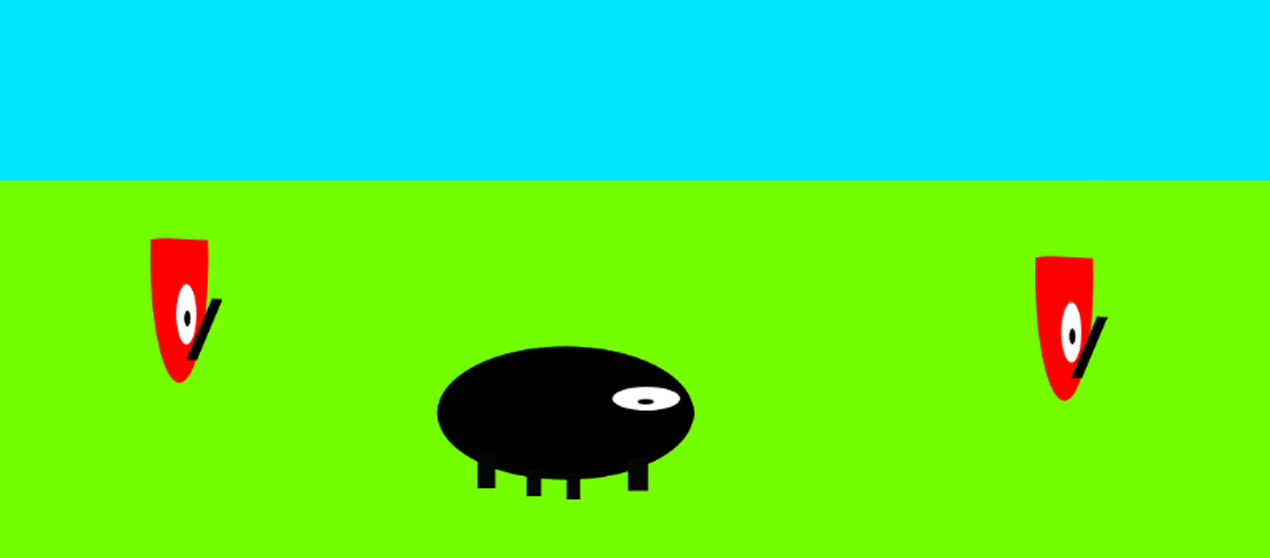


My 10 year-old son made this game in the language Scratch in a few hours (with some help). Neither of us had coded in Scratch before, and I hadn't really seen it before at all. At...
This page gives a quick introduction to the Iptables firewall software for Linux. More details will follow later... 1. How Iptables Works. The term “iptables” may refer to either the software firewall which is integrated...
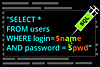
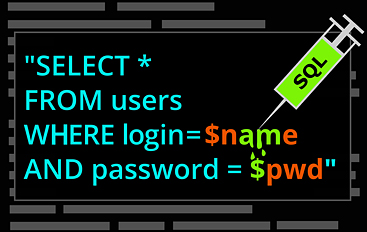
Basics of SQL Injection Attacks
SQL injection attacks are carried out by inserting SQL code into a field where user input is accepted. If the user input is not correctly handled, this can result in the code executing by the...

 Welcome to Byte Yoga, my blog about Coding, Computers and IT.
Welcome to Byte Yoga, my blog about Coding, Computers and IT.
 Spysafe.com.au and Codewiz.au have become Byte Yoga!
Spysafe.com.au and Codewiz.au have become Byte Yoga!
 View My Programmer and Full Stack Developer Portfolio.
View My Programmer and Full Stack Developer Portfolio.
 About Byte Yoga – IT, Coding, tech, security, careers, and stuff.
About Byte Yoga – IT, Coding, tech, security, careers, and stuff.