3 Articles in the category: Injection
bWAPP – A Deliberately Buggy Web App to Practice Cybersecurity
Mon, 10th of January 2022 11:20 PMThis page describes how to install bee-box, a virtual Linux installation containing bWAPP, which is a deliberately buggy web application to practice pentesting and other cyber security skills on. From the bWAPP website: ...
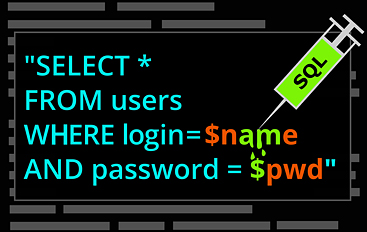
Basics of SQL Injection Attacks
Mon, 3rd of January 2022 8:15 PMSQL injection attacks are carried out by inserting SQL code into a field where user input is accepted. If the user input is not correctly handled, this can result in the code executing by the...
Log4Shell – The Single Biggest Security Vulnerability Ever?
Tue, 21st of December 2021 1:14 PMLog4Shell is a recently disclosed security vulnerability in a popular piece of software used for generating log files (including logging error messages), written in Java, known as Log4j. It's affected countless computers around the world...

 Welcome to Byte Yoga, my blog about Coding, Computers and IT.
Welcome to Byte Yoga, my blog about Coding, Computers and IT.
 Spysafe.com.au and Codewiz.au have become Byte Yoga!
Spysafe.com.au and Codewiz.au have become Byte Yoga!
 View My Programmer and Full Stack Developer Portfolio.
View My Programmer and Full Stack Developer Portfolio.
 About Byte Yoga – IT, Coding, tech, security, careers, and stuff.
About Byte Yoga – IT, Coding, tech, security, careers, and stuff.